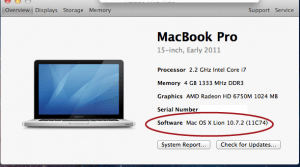
- Invisible Apartment 3 Mac Os Download
- Apartment 3 Bar
- Invisible Apartment 3 Mac Os Install
- Invisible Apartment 3 Mac Os Versions
- Invisible Apartment 3 Mac Os X
Discover the innovative world of Apple and shop everything iPhone, iPad, Apple Watch, Mac, and Apple TV, plus explore accessories, entertainment, and expert device support. What's your Mac been up to for the last 3 months? Inside macOS's hidden activity records If you've got problems with your Mac and use Apple Support, one thing they're likely to do is run sysdiagnose on it: it even has its own keystroke combination, of Command-Option-Control-Shift. If you liked Invisible Apartment 1 and would like to get a continuation of the story, than download and install the other chapters Invisible Apartment 2 & 3 and the prequel Invisible Apartment Zero as DLC. Modern versions of Mac OS offer a very convenient way to hide/unhide files and folders on Mac, all that you have to is press a couple of magic buttons, and that is it. This is by far the fastest and most efficient way to add files to a hidden folder or have access to one. How to show hidden files on a Mac We explain how to see hidden files and the /Library folder so you can make adjustments. But beware, they are hidden for a reason.
Wireless
The wireless section is used to configure the wireless settings for your D-Link router. Note that changes made in this section may also need to be duplicated on wireless clients that you want to connect to your wireless network.
To protect your privacy, use the wireless security mode to configure the wireless security features. This device supports three wireless security modes including: WEP, WPA-Personal, and WPA-Enterprise. WEP is the original wireless encryption standard. WPA provides a higher level of security. WPA-Personal does not require an authentication server. The WPA-Enterprise option does require a RADIUS authentication server.
A method of encrypting data for wireless communication intended to provide the same level of privacy as a wired network. WEP is not as secure as WPA encryption. To gain access to a WEP network, you must know the key. The key is a string of characters that you create. When using WEP, you must determine the level of encryption. The type of encryption determines the key length. 128-bit encryption requires a longer key than 64-bit encryption. Keys are defined by entering in a string in HEX (hexadecimal - using characters 0-9, A-F) or ASCII (American Standard Code for Information Interchange - alphanumeric characters) format. ASCII format is provided so you can enter a string that is easier to remember. The ASCII string is converted to HEX for use over the network. Four keys can be defined so that you can change keys easily. A default key is selected for use on the network.
- Example:
- 64-bit hexadecimal keys are exactly 10 characters in length. (12345678FA is a valid string of 10 characters for 64-bit encryption.)
- 128-bit hexadecimal keys are exactly 26 characters in length. (456FBCDF123400122225271730 is a valid string of 26 characters for 128-bit encryption.)
- 64-bit ASCII keys are up to 5 characters in length (DMODE is a valid string of 5 characters for 64-bit encryption.)
- 128-bit ASCII keys are up to 13 characters in length (2002HALOSWIN1 is a valid string of 13 characters for 128-bit encryption.)
Note that, if you enter fewer characters in the WEP key than required, the remainder of the key is automatically padded with zeros.
Both of these options select some variant of Wi-Fi Protected Access (WPA) -- security standards published by the Wi-Fi Alliance. The WPA Mode further refines the variant that the router should employ.
WPA Mode: WPA is the older standard; select this option if the clients that will be used with the router only support the older standard. WPA2 is the newer implementation of the stronger IEEE 802.11i security standard. With the 'WPA2' option, the router tries WPA2 first, but falls back to WPA if the client only supports WPA. With the 'WPA2 Only' option, the router associates only with clients that also support WPA2 security.
Group Key Update Interval: The amount of time before the group key used for broadcast and multicast data is changed.
This option uses Wi-Fi Protected Access with a Pre-Shared Key (PSK).
Pre-Shared Key: The key is entered as a pass-phrase of up to 63 alphanumeric characters in ASCII (American Standard Code for Information Interchange) format at both ends of the wireless connection. It cannot be shorter than eight characters, although for proper security it needs to be of ample length and should not be a commonly known phrase. This phrase is used to generate session keys that are unique for each wireless client.
- Example:
Wireless Networking technology enables ubiquitous communication
This option works with a RADIUS Server to authenticate wireless clients. Wireless clients should have established the necessary credentials before attempting to authenticate to the Server through this Gateway. Furthermore, it may be necessary to configure the RADIUS Server to allow this Gateway to authenticate users.
Authentication Timeout: Amount of time before a client will be required to re-authenticate.
RADIUS Server IP Address: The IP address of the authentication server.
Invisible Apartment 3 Mac Os Download
RADIUS Server Port: The port number used to connect to the authentication server.
Apartment 3 Bar
RADIUS Server Shared Secret: A pass-phrase that must match with the authentication server. Machine at the heart of the world mac os.
MAC Address Authentication: If this is selected, the user must connect from the same computer whenever logging into the wireless network.
Advanced:
- Optional Backup RADIUS Server
- This option enables configuration of an optional second RADIUS server. A second RADIUS server can be used as backup for the primary RADIUS server. The second RADIUS server is consulted only when the primary server is not available or not responding. The fields Second RADIUS Server IP Address, RADIUS Server Port, Second RADIUS server Shared Secret, Second MAC Address Authentication provide the corresponding parameters for the second RADIUS Server.
iPad Pro
Supercharged by the Apple M1 chip.
RADIUS Server IP Address: The IP address of the authentication server.
Invisible Apartment 3 Mac Os Download
RADIUS Server Port: The port number used to connect to the authentication server.
Apartment 3 Bar
RADIUS Server Shared Secret: A pass-phrase that must match with the authentication server. Machine at the heart of the world mac os.
MAC Address Authentication: If this is selected, the user must connect from the same computer whenever logging into the wireless network.
Advanced:
- Optional Backup RADIUS Server
- This option enables configuration of an optional second RADIUS server. A second RADIUS server can be used as backup for the primary RADIUS server. The second RADIUS server is consulted only when the primary server is not available or not responding. The fields Second RADIUS Server IP Address, RADIUS Server Port, Second RADIUS server Shared Secret, Second MAC Address Authentication provide the corresponding parameters for the second RADIUS Server.
iPad Pro
Supercharged by the Apple M1 chip.
iPhone 12
Purple. Now in season.
From $29.12/mo. for 24 mo. or $699 before trade‑in1
Buy directly from Apple with special carrier offers

